Navigating Data Privacy in Generative AI
Summary
Artificial intelligence has come a long way since it was first introduced in the 1950s. However, these developments raise concerns about bias, equity, and data privacy. Feeding sensitive data to large language models (LLMs) carries risks, including non-removable data and compliance problems. Businesses need to put in place robust AI privacy policies to protect personally identifiable information (PII) and make the most of AI technologies.
Key insights:
Foundational Developments: Artificial Intelligence started in the 1950s and progressed from early ideas such as Hidden Markov Models to deep learning methods. Generative AI emerged in the latter half of the 20th century, allowing machines to produce a variety of outputs.
Impact of Generative AI: With over 100 million people quickly embracing the application after its November 2022 launch, ChatGPT represented a major turning point in the rapidly expanding accessibility and use of AI technologies.
Data Privacy Concerns: Significant worries about bias, fairness, and data privacy are brought up by the quick development of AI technology, especially as large language models (LLMs) grow more intricate and are incorporated into more applications.
Data Privacy Challenges: When sensitive data is integrated into LLMs, there are several risks involved. These risks include the inability to completely remove the data, problems with regulatory compliance such as GDPR and CCPA violations, the possibility of internal information being revealed, and limits on innovation that can make it more difficult for businesses to successfully investigate new AI models.
Data Privacy Vault: A comprehensive solution called a Data Privacy Vault allows businesses to use cutting-edge AI technology while securely managing sensitive data. It ensures compliance and efficient use of data without compromising privacy by incorporating crucial elements like isolation, encryption, governance, and a structured operational framework for data ingestion, processing, and output management.
Introduction
The journey towards artificial intelligence (AI) began in the 1950s with the development of important advances such as hidden Markov models and Gaussian mixture models. Over time, the field has seen transformation, with the advent of deep learning techniques. The launch of ChatGPT in November 2022, attracted over 100 million users in two months. This marked a turning point in the evolution of AI. The rapid advancements in AI have raised questions of fairness, bias, and data privacy.
The paper From ChatGPT to ThreatGPT: Impact of Generative AI in Cybersecurity and Privacy highlights the importance of addressing data privacy issues in generative AI tools. If not used appropriately, these technologies can expose personal user information. It was shown that ChatGPT is vulnerable to attacks (prompt injection and social engineering) that can lead to the exfiltration of private data. The sophistication of generative AI models necessitates a reevaluation of privacy-enhancing technologies (PETs) and the development of new data protection techniques.
This article aims to provide an overview of the importance of data privacy when interacting with AI technologies, best practices to safeguard data, and an analysis of four data security privacy platforms for generative AI.
Risks of Feeding Sensitive Data to LLMs
In her analysis, “Risks of Feeding Sensitive Data to LLMs,” Amruta Moktali explains the risks involved in integrating sensitive data into large language models (LLMs) :
1. Lack of a Delete Button
It is difficult to delete sensitive material from a large language model (LLM) without retraining it once it has been ingested. Because it is impossible to remove sensitive data that has unintentionally entered the training set, this feature carries a high risk. Retraining requires a lot of resources and might not ensure that all sensitive data is removed from the model's outputs, which could result in privacy violations.
2. Compliance Requirements
The processing of sensitive data needs to comply with requirements like the General Data Protection Regulation (GDPR), Payment Card Industry (PCI) standards, and Service Organization Control 2 (SOC2). These enforce guidelines for the handling of PII. Businesses must have strong data privacy policies in place since non-compliance can result in harsh fines and a loss of customer trust.
3. Internal and IP Data
When firms feed intellectual property (IP) or internal business data into LLMs, they run the danger of revealing confidential information. For example, Samsung's ChatGPT experience brought to light the risks associated with disclosing product roadmaps and project code names. The significance of safeguarding internal data is highlighted by the possibility of trade secret theft and competitive disadvantages as a result of this disclosure.
4. Impact on Flexibility
The way a business handles data privacy issues has a big influence on how much it can experiment with new AI models. Organizations frequently encounter limitations when choosing a model when dealing with sensitive data since they have to take privacy and regulatory concerns into account. This restriction may impede creativity and the efficient application of various LLMs customized for certain use cases, which may ultimately impair a company's ability to quickly adopt new technology.
Data Privacy Vault
A Data Privacy Vault is a tool made to keep private data safe from prying eyes. This idea is essential to guaranteeing that businesses can use AI and machine learning, without jeopardizing the privacy of sensitive information, like personally identifiable information (PII).
1. Components of a Data Privacy Vault
A Data Privacy Vault consists of several elements, each of which is vital to data protection:
Isolation: The vault reduces the breadth of compliance requirements and the attack surface by isolating sensitive data from other systems. To make sure that unauthorized parties cannot readily access sensitive information, this isolation is essential.
Protection: To safeguard data, the vault uses strong methods including encryption, masking, and tokenization. These methods guarantee that private information stays private even if unauthorized parties gain access to it.
Governance: The vault is equipped with fine-grained access controls to limit who can access what information. By limiting access to sensitive information to just authorized workers, this governance lowers the possibility of data misuse.
Localization: Organizations can effectively manage sensitive data while adhering to data residency laws by utilizing regional vault instances. Businesses can store data locally by using this component, which eliminates the need for entire infrastructure replication across several locations.
2. How the Vault Works
The operational architecture of a Data Privacy Vault consists of several key phases that provide data protection top priority throughout the data lifecycle:
Ingestion and Storage: Sensitive data is instantly isolated at the moment of ingestion. Sensitive data is collected easier with the help of the APIs or SDKs, which point it toward the vault for safekeeping.
Processing: Sensitive data is tokenized or redacted during processing to guarantee its security when used by AI or machine learning techniques. For data privacy to be maintained throughout the data lifespan, this step is essential.
Output Management: The vault can produce actual data in place of pseudonymized data as needed. Businesses can use the data without jeopardizing sensitive information as a result of this selective dissemination.
3. The Need for an AI Privacy Strategy
Organizations of all sizes must create a strong AI privacy strategy in light of the incorporation of AI technologies. An essential part of this strategy is a Data Privacy Vault, which helps businesses de-identify sensitive data and make good use of public LLMs. Smaller businesses can gain a competitive edge by quickly implementing data privacy protections because it frees them from having to train their models to use AI.
It is critical to realize that protecting AI data privacy cannot be approached as a band-aid or expedient fix. From initial data collection to model training and inference, organizations must make sure that data privacy and security protections are included across the whole data lifecycle.
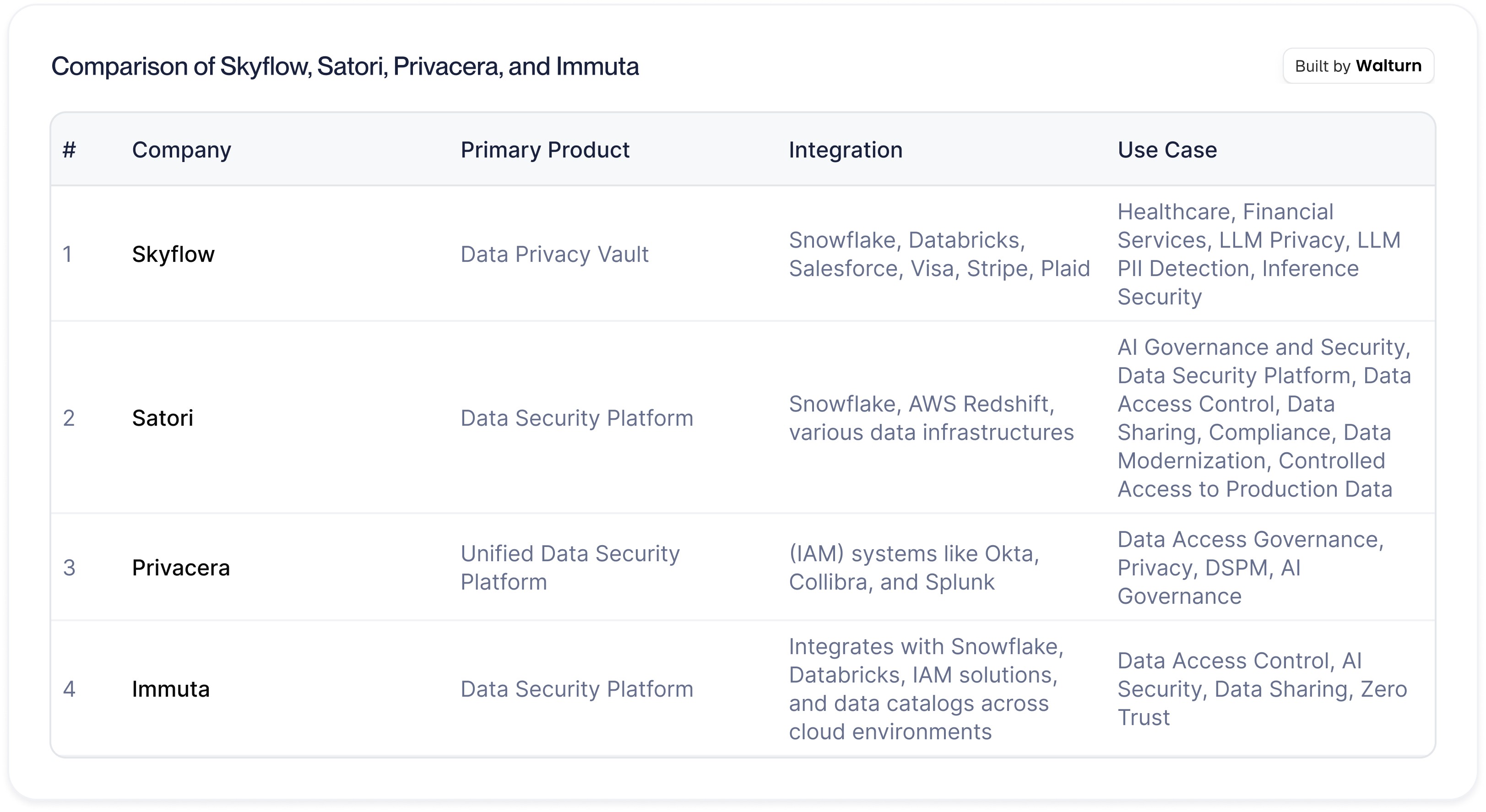
Data Security Platforms for GenAI
1. Skyflow
Secure workflows for exchanging and managing sensitive data are made possible with Skyflow. This includes the capacity to operate custom code, de-identify data, and integrate third-party services—all within a safe and legal environment. Skyflow assists companies with safeguarding confidential financial information, and PII across workflows, adhering to international data residency laws, and safely integrating LLMs. Whether it is used for AI-driven use cases, payments, or healthcare, the vault streamlines operations while lowering regulatory requirements.
Skyflow offers several products including the following:
Skyflow Data Privacy Vault: Skyflow's main product is a Data Privacy Vault. It is a scalable, secure solution that manages, safeguards and isolates sensitive data across several applications while guaranteeing compliance with international laws. Businesses may tokenize, encrypt, and manage Payment Card Industry (PCI) and Personally Identifiable Information (PII) data without sacrificing usability for analytics or operations by using the vault's straightforward API.
Compliance Solutions: Skyflow's vault isolates and manages sensitive data with automated audit logging, fine-grained access restrictions, and governance standards, enabling compliance with stringent global data protection regulations including GDPR, CCPA, HIPAA, and PCI DSS. It keeps data residency while simplifying the process of satisfying regulatory requirements.
APIs for Privacy Management: Developers may easily include data privacy in any application with the help of the API-driven platform. Encrypting, tokenizing, managing, and de-identifying sensitive data is made easy with Skyflow's suite of APIs, which guarantee data security throughout your whole tech stack—in transit, at rest, and in use.
Integration: Leading technologies like Salesforce, Databricks, and Snowflake, as well as payment processors like Visa, Stripe, and Plaid, all easily interface with Skyflow. These interfaces reduce compliance risks, increase productivity, and help businesses optimize their data workflows while protecting personally identifiable information (PII) and keeping it out of operational databases.
Developer-Friendly SDKs: To facilitate integration with the vault, Skyflow provides SDKs for several platforms, including Android, iOS, and server-side frameworks. This makes it simpler for developers to include security measures and privacy in their apps. Tokenization, de-tokenization, and controlling sensitive data transfers between systems are all included in this.
LLM (Large Language Models): The protection of private data throughout the phases of AI data gathering, training, fine-tuning, and inference is the main goal of Skyflow's LLM solutions. Organizations can use ChatGPT and other generative AI models without jeopardizing PII or intellectual property (IP) by redacting sensitive data.
Skyflow’s use cases extend across various industries including:
Healthcare: Skyflow's vault securely stores sensitive patient data, assisting healthcare providers in adhering to HIPAA regulations. Businesses may safely analyze healthcare data, improve patient care, and train AI models without running the risk of privacy breaches by tokenizing and de-identifying personally identifiable information.
Financial Services (Protect Payments): Skyflow makes PCI compliance easier by enclosing and safeguarding payment information in the vault. It combines with payment systems to guarantee that companies maintain control over their payment data while lowering fraud, enabling secure card issuance, and facilitating safe money transfers.
LLM Privacy: Skyflow makes sure that LLM training datasets do not contain sensitive information like PII and IP. Businesses can employ generative AI without running the risk of disclosing confidential or proprietary information by de-identifying data and applying governance throughout LLM inference.
LLM PII Detection: Skyflow ensures that LLMs comply with privacy requirements and do not inadvertently keep or misuse personal information by identifying and de-identifying sensitive data during AI model training and inference.
Inference Security: To maintain the functionality and compliance of AI implementations, sensitive data is securely censored during LLM inference procedures, with re-identification permitted only for authorized persons.
2. Satori
By automating controls, security, and compliance needs throughout the data infrastructure, the Satori Data Security Platform helps engineering and security teams streamline data access. Satori is essentially a universal data security and access service that is made to track, categorize, and manage sensitive data access. It is designed for businesses where BI teams, analysts, and data scientists need to access vital information for the development of new products and services.
To monitor and manage access, Satori adds a transparent layer on top of popular data stores (like Snowflake and AWS Redshift). For every data store, it creates a special URL that Satori provides, which users may access without changing their workspace.
Its key features include:
AI Security Platform: The use of AI in business brings with it new security risks, especially when it comes to the exposure of sensitive data. Satori's AI Security Platform provides visibility and control over AI systems, guaranteeing safe data operations and access for AI teams. Businesses can simplify access restrictions for AI models with AI Access Policy Management, and reduce risks by having complete insight into interactions with large language models using LLM Activity Monitoring. This platform enables teams to safely build and implement AI applications without sacrificing data integrity, resulting in faster AI-driven innovation.
Temporary Data Access: Security and compliance issues are greatly increased when sensitive data is persistently accessible. With integrated automatic approvals, Satori's Temporary Data Access solution offers safe, on-demand access to data. Self-service features let users choose datasets and get access right away while applying security policies dynamically. Data engineers can save time and increase productivity with this just-in-time access. With fewer bottlenecks in AI and analytics initiatives, teams may more swiftly and safely utilize the data they require.
Data Access Control: Handling access to data in various data contexts can be difficult and time-consuming. By centralizing access control, Satori's Data Access Control solution makes it simple for teams to scale rights across BI tools and data repositories. Advanced security features including Attribute-dependent Access Control (ABAC) for user-specific access and Dynamic Data Masking, which dynamically applies masking policies depending on data kinds and identities, are supported. Furthermore, Row-Level Security (RLS) makes it easier for enterprises to comply with granular security requirements, allowing them to implement strong data governance without interfering with processes.
Data Classification & Discovery: It takes a lot of time and resources to manually locate and classify sensitive data across several data warehouses, and it can also be error-prone. This procedure is automated by Satori's Data Classification & Discovery tool, which continuously scans data environments to update inventories and implement security regulations. It guarantees that sensitive material is recognized and safeguarded by integrating with current data catalogs and supporting custom classifiers. Businesses can utilize Satori to avoid unauthorized data access, streamline compliance with data protection laws, and facilitate secure data access for analytics and artificial intelligence use cases.
Dynamic Data Masking: By automating data masking without requiring code changes, Satori's Dynamic Data Masking solution streamlines the process of securing sensitive information. Its scalable methodology expedites AI and analytics activities by guaranteeing that data is constantly safe across many storages. Masking policies can be readily created, modified, and maintained by users, preventing unauthorized access to confidential information. Satori helps businesses comply with regulations by offering real-time masking depending on user responsibilities and data sensitivity, enabling teams to safely access and work with the data they require.
Data Activity Audit & Monitoring: By giving businesses total insight into data access activity, Satori's Data Activity Audit & Monitoring solution drastically cuts down on the amount of time needed for compliance audits. Deeper insights into data consumption patterns are made possible by its richer reporting and Universal Data Access Audit, which makes tracking data access logs across numerous data repositories easier. By using this platform, firms can make sure they comply with regulatory standards and comprehend the entire context of data access, which helps to proactively address possible security and compliance issues.
Posture Management: Maintaining an appropriate data security posture is essential, but figuring out who might have access to your data can be difficult. With the help of the Universal Data Permissions Scanner (UDPS), Satori's Posture Management solution provides a real-time picture of data permissions and can rapidly detect access hazards. To proactively reduce security risks, organizations should also find data stores throughout their architecture and examine permissions. Satori helps businesses maintain strict security controls and fulfill compliance requirements by offering comprehensive visibility into who can access what data.
Satori can be used in various use cases documented below.
AI Governance and Security: Security and governance are essential elements in the battle to incorporate AI into corporate operations that guarantee ethical and seamless AI deployments. With the help of Satori's Data Security Platform, businesses can establish strong security rules since they have visibility and control over their data. Satori assists companies in safeguarding confidential information, adhering to legal requirements, and quickly expanding their AI projects by guaranteeing that AI models are managed with unambiguous access rules. Satori guarantees AI dependability by dynamically enforcing security standards like data redaction, freeing data teams to concentrate on innovation without sacrificing governance or security.
Data Security Platform: Data teams now have a comprehensive way to access, manage, and safeguard their data while optimizing its value for analytics and artificial intelligence (AI) by using Satori's Data Security Platform. With features like data masking and row-level security, the platform offers hands-off data access while maintaining security, enabling users to work fast and effectively. Data engineers may concentrate more on business objectives and spend less time manually managing access with Satori. This platform ensures that businesses maintain control over their data governance even as they experiment with artificial intelligence and analytics by supporting a broad range of data environments.
Data Access Control: AI and analytics projects may be slowed down by manual data access procedures, which can result in decreased productivity and missed opportunities. These bottlenecks are removed by Satori's Data Access Control system, which offers quick, safe access to data via an easy-to-use data gateway. Organizations can expedite access while upholding rigorous governance over sensitive data by enforcing dynamic control. Through the automation of security and access controls, Satori speeds up AI readiness without sacrificing control or compliance, freeing up data teams to work on higher-value projects.
Data Sharing: Satori eliminates one of the largest obstacles to AI and analytics initiatives by facilitating quick, safe, and effective data sharing. Rather than depending on laborious manual procedures that hinder cooperation and pose security threats, Satori's platform facilitates prompt, controlled access to information from various sources, such as databases, warehouses, and data lakes. Satori's capabilities, which include data masking and approval protocols, guarantee that data can be exchanged securely without compromising security or compliance, allowing teams to fully utilize their data.
Data Compliance: Manually meeting data compliance requirements is a laborious and prone-to-error process that frequently causes delays in business efforts and audits. Satori provides teams with complete control over who can access sensitive data and why, automating compliance with off-the-shelf alternatives. Satori lowers compliance risks and saves weeks of preparation by ensuring that firms are always prepared for audits through continuous monitoring and quick reporting. This automation guarantees data security in all AI and analytics workflows while also simplifying compliance.
Data Modernization: Keeping control over data access and security can get more difficult as businesses update their data platforms. By providing a governance platform that functions flawlessly across contemporary data architectures, including cloud migrations, Satori streamlines this process. Satori facilitates the shift to data environments that are more agile and AI-ready by allowing quick and safe access to data. Its dynamic access controls help organizations realize the full value of their data by ensuring that sensitive information is safeguarded throughout the modernization process.
Controlled Access to Production Data: To solve problems or enhance systems, engineers usually want quick access to production data; nevertheless, this data frequently includes sensitive information, such as consumer PII. The platform from Satori enforces dynamic regulations like data masking and temporary access authorization to guarantee regulated, secure access to production data. This maintains compliance and security standards, enables engineers to work rapidly without disclosing sensitive information, and guarantees that production concerns are promptly fixed.
Integration: Leading tools like AWS, Collibra, Slack, and Microsoft Security Copilot are all easy to integrate with Satori. Additionally, Satori's REST API enables programmatic interaction between developers and the platform, facilitating the automation of different security and data access activities.
3. Privacera
To safeguard confidential information and streamline access control, Privacera provides an extensive range of data security and access governance solutions. The Unified Data Security Platform from Privacera, which combines data discovery, encryption, access control, and processes to streamline data governance in a variety of settings, is the central component. It is based on open standards and makes use of Apache Ranger to reduce vendor lock-in and guarantee interoperability with a variety of data ecosystems. It supports a range of data sources, including cloud-native, multi-cloud, and on-premises systems, with more than 50 native connections. Along with sophisticated capabilities for GenAI governance, key offerings include Data Access Governance, Data Privacy and Compliance, Federated Data Stewardship, and Data Security Posture Management (DSPM).
Here are some key features and use cases of Privacera:
Data Access Governance: By combining coarse and fine-grained access restrictions, Privacera centralizes data access management and guarantees that users have the proper amount of access to sensitive material. This keeps data from being overshared and allows for quick, safe access to the data that is needed.
Data Privacy and Compliance: To comply with the GDPR, CCPA, HIPAA, and other regulations, the platform automates the identification of Personally Identifiable Information (PII) and applies worldwide data privacy requirements. Establishing system-wide standards allows organizations to safeguard confidential data while guaranteeing compliance in various legal jurisdictions.
Data Security Posture Management (DSPM): Privacera is used by security teams to audit, monitor, and improve their data security posture constantly. To lessen security threats, the platform finds vulnerabilities, evaluates risks and implements encryption, masking, and access control procedures.
Federated Data Stewardship: Privacera facilitates the decentralized administration of data security policies, giving data owners and stewards the authority to establish access rules that are specific to their businesses while adhering to general regulations.
GenAI Governance: Privacera's AI Governance module assists in safeguarding intellectual property, identifying security risks, and guaranteeing adherence to PII requirements throughout the training and implementation of AI models, as generative AI gains traction.
Integration: Comprehensive coverage is made possible by Privacera's platform's easy integration with current enterprise data governance and security frameworks. Popular identity and access management (IAM) platforms like Okta, data catalogs like Collibra, and security analytics tools like Splunk are all supported for integration. Additionally, the platform provides native enforcement, which lets businesses apply data security guidelines throughout their whole ecosystem without interfering with data pipelines or query paths already in place. Its architecture, which is built on open standards, makes it future-proof for changing data security requirements by ensuring flexibility for integration with a wide range of enterprise systems and reducing complexity.
4. Immuta
Immuta is a helpful resource for businesses that integrate AI and ML technologies. It provides a comprehensive data security platform that aims to safeguard, identify, and uncover critical data. The platform assists in controlling data access across cloud infrastructure by providing dynamic, policy-driven security and privacy controls. By utilizing Immuta, businesses can enforce strong security rules and ensure compliance with privacy laws such as GDPR and HIPAA.
Additionally, Immuta's dynamic access control streamlines data governance by automating numerous areas of data security management and requiring up to 93 times fewer policies than standard role-based access control solutions.
Immuta’s key features include the following:
Sensitive Data Discovery & Classification: With the help of more than 60 pre-built classifiers designed with particular demands for the industry, Immuta's platform automatically finds and categorizes sensitive data. This feature facilitates compliance with privacy standards by ensuring that firms are aware of exactly what sensitive data they have and can put the necessary safeguards in place.
Dynamic Data Masking: Immuta's dynamic data masking technology, which alters or conceals data values in real time without affecting the underlying datasets, safeguards critical information. This permits companies to support profitable use cases, such as analytics or training AI models, while ensuring safe access to data without compromising security or privacy.
Attribute-Based Access Control (ABAC): Unlike role-based access control (RBAC), which can result in an overabundance of roles, Immuta's ABAC provides a more flexible, scalable, and efficient approach to controlling access to data. ABAC is the ideal option for companies handling complex data ecosystems since policies are based on user attributes such as role, clearance level, and location. Immuta's ABAC replaces hundreds of security rules with a single policy, greatly reducing the time and resources required to manage access.
Data Use Tracking & Remediation: Immuta monitors all requests, policy applications, and data consumption. It makes it easier to spot anomalies, investigate incidents, and take corrective action because it provides an extensive audit trail. This feature makes it easier to comply with legal and regulatory requirements by giving a clear picture of how data is accessed and utilized within the company.
Continuous Data Security Monitoring: Businesses can spot threats and take preemptive action by utilizing Immuta's real-time insights into user behavior and data access. Because of its anomaly detection capabilities, security experts can respond quickly and effectively to any unusual data usage trends.
Privacy Enhancing Technologies (PETs): Immuta's PETs provide dynamic masking and anonymization of sensitive data through techniques including k-anonymization, pseudonymization, and differential privacy. Businesses that need to share data while maintaining privacy protections must use these technologies, especially those in heavily regulated industries like healthcare and banking.
Plain Language Policy Authoring: Immuta makes it easy to establish and administer data policies by offering a policy builder that lets users write policies in simple language. This facilitates better communication between the technical and governance teams by decreasing the complexity and increasing the manageability of data security for non-technical stakeholders.
Seamless Cloud Governance: All cloud data, independent of the cloud infrastructure being used (such as AWS, GCP, or Azure), can be governed by Immuta's platform. Organizations can ensure compliance and streamline operations by maintaining a uniform security posture across various cloud environments by using Immuta’s integrated governance architecture.
Integration: Immuta supports AI and data projects with next-generation data security by integrating easily with top cloud data platforms like Snowflake and Databricks. Immuta guarantees that businesses can swiftly and effectively manage and grow AI-based apps securely by supporting integration with Snowflake. Likewise, Immuta facilitates the fusion of data and AI by working with Databricks to provide platform improvements that meet enterprise requirements for security and performance.
Below are some use cases that demonstrate the practical applications of Immuta’s data management solutions.
Implementing Dynamic Data Access Control at Scale: Data access control, an essential component of data security, governs who may see, access, and utilize what data within a system or database. Implementing effective data access control starts with identifying and classifying sensitive data. Next, policies that uphold access authorization are put in place. Traditional static role-based controls are no longer sufficient due to the exponential rise of data volumes and legal requirements, which has resulted in issues like role explosion and manual management. With Immuta's attribute-based access control (ABAC), enterprises can effectively safeguard their data while enabling user access. This dynamic and scalable solution lowers the cost of managing policies and improves compliance.
Securing Data for AI Model Training and Deployment: Data security for artificial intelligence (AI) systems is becoming increasingly important as AI continues to change how businesses run. To effectively deploy AI technologies, companies must handle the serious dangers posed by AI security concerns, such as biased decision-making and illegal model use. Businesses may safeguard sensitive data and enable secure AI model training and deployment by putting in place robust data security solutions, such as those offered by Immuta. Organizations can control the data utilized in AI applications by using Immuta's sophisticated data classification and tagging capabilities. This promotes privacy legislation compliance, builds system trust, and eventually leads to the successful adoption of AI.
Enabling Decentralized Data Governance with Data Mesh: Data mesh is a paradigm change in data management that promotes a decentralized strategy that divides data ownership and control among several teams inside a company. This method maintains essential security and compliance standards while addressing the challenges of handling data in big, distributed contexts. By offering a single control layer for policy administration, Immuta supports data mesh architectures and enables self-service data access while enabling enterprises to enforce governance. With the help of this federated architecture, domain owners may safely manage their data products, guaranteeing efficiency and compliance without having to resort to laborious centralized controls.
Proactive Risk Management: To keep a strong security posture in the face of increasingly complex data environments, enterprises must implement Data Security Posture Management (DSPM). Security teams can proactively address vulnerabilities by leveraging Immuta's DSPM capabilities, which enable continuous monitoring of data usage and real-time risk assessments based on data sensitivity. Due to a lack of policy enforcement, traditional DSPM technologies frequently fail, resulting in laborious, lengthy remediation processes. This gap is filled by Immuta, which offers an integrated platform for managing policies and monitoring data, enabling enterprises to quickly detect and address problems related to data access while maintaining compliance and protecting sensitive data.
Secure and Compliant Data Sharing Across Organizations: In the linked world of today, data sharing is an essential procedure that allows businesses to work together efficiently and gain knowledge from shared information. However, there are several obstacles to overcome in assuring the secure sharing of data, especially in highly regulated businesses. Secure data sharing is made possible by Immuta's dynamic data masking capabilities and privacy-enhancing technologies, which guarantee the protection of sensitive data both in transit and at rest. Organizations can improve cooperation and innovation while reducing the dangers of data exploitation by putting in place purpose-based access rules and upholding an open framework for data exchange.
Regulatory Compliance in Data-Intensive Industries: As businesses traverse the complicated web of regulations governing data use and protection, regulatory compliance is a top priority. Organizations are required to comply with a growing number of regulations due to the widespread usage of data and the escalating dangers. This frequently leads to laborious and prone errors in manual operations. Immuta facilitates compliance efforts by offering sophisticated enforcement and policy management features that let businesses keep an eye on and audit data usage in real time. Immuta enables businesses to safeguard sensitive data while upholding stakeholder and consumer trust by making compliance with laws like GDPR and HIPAA easier.
Adopting Zero Trust Data Security: A new architecture called "zero trust data security" stresses the idea of "never trust, always verify," making sure that every data access is regularly verified regardless of the user's position or role. Although this practice improves security, it can be difficult to execute, especially in distributed cloud environments. Immuta facilitates the adoption of Zero Trust by offering tools for simple policy creation in plain English and facilitating smooth interfaces with top data platforms. In addition to improving security, this strategy enables enterprises to roll out self-service data access on a large scale, guaranteeing that the appropriate people can access the appropriate data for legal reasons without jeopardizing security or compliance.
Conclusion
In conclusion, the swift advancement of artificial intelligence (AI), especially with the emergence of generative AI and large language models (LLMs), has tremendous potential for a variety of businesses. But it has also brought up serious issues with data privacy. These difficulties include adhering to strict privacy laws, the dangers of feeding sensitive material into LLMs, and the absence of procedures to remove such data. Businesses must manage these risks as LLM adoption rises in order to safeguard confidential data while preserving operational flexibility. Solutions like tokenization, data privacy vaults, and privacy-enhancing technologies (PETs) have become indispensable instruments for enabling enterprises to securely use AI without jeopardizing intellectual property or personally identifiable information (PII).
Innovative solutions have been developed by companies such as Immuta, Privacera, Satori, and Skyflow to address these privacy concerns. For example, Skyflow's Data Privacy Vault provides a safe and legal means of handling private information, allowing companies to use public LLMs legally and comply with regulations. Organizations must prioritize an integrated AI privacy plan that covers the safe handling of sensitive data at every stage of its lifecycle as AI technologies progress. By doing this, companies can protect customer trust and adhere to regulatory regulations while realizing AI's full potential.
Authors
Secure Your AI Solutions with Walturn
Transform your AI capabilities with Walturn's expertise in secure integration of generative AI tools. We specialize in implementing robust safeguards and encryption protocols to protect sensitive data while customizing models for specific tasks and domains. Our approach ensures delivery of precise, context-aware results tailored to your needs, all within a highly secure framework. Partner with Walturn to leverage cutting-edge AI technologies, optimize performance, and drive innovation in your business while maintaining the highest standards of data protection and privacy compliance.
References
“GigaOm Report Reveals Advantages of Modern Approach to Data Access Control.” Businesswire, 25 Jan. 2023, www.businesswire.com/news/home/20230125005317/en/GigaOm-Report-Reveals-Advantages-of-Modern-Approach-to-Data-Access-Control.
Gupta, Maanak, et al. “From ChatGPT to ThreatGPT: Impact of Generative AI in Cybersecurity and Privacy.” IEEE Access, vol. 11, Jan. 2023, pp. 80218–45. https://doi.org/10.1109/access.2023.3300381.
Immuta. “De-risk Your Data | Immuta.” Immuta, 29 Aug. 2024, www.immuta.com.
Moktali, Amruta. “AI Data Privacy: A New Product Essential.” Mind the Product, 17 Oct. 2023, www.mindtheproduct.com/ai-data-privacy-a-new-product-essential.
Privacera. “Privacera - Data Security, Access Control, Privacy Compliance.” Privacera, 30 Apr. 2024, privacera.com.
Satori Cyber. “Satori | Data Security Platform.” Satori, 1 July 2024, satoricyber.com.
Skyflow | Don’t DIY PII. www.skyflow.com.