Ensuring HIPAA Compliance in Product Development
Summary
HIPAA compliance requires integrating security throughout healthcare app development. This guide covers implementing HIPAA standards across all stages, from planning to maintenance. Key focus areas include Privacy and Security Rules, secure design, engineering protocols, and testing. Early compliance planning and ongoing monitoring help protect patient data and build user trust.
Key insights:
Comprehensive Compliance: HIPAA requires continuous attention to PHI security, embedding compliance in each development phase, from planning to post-launch.
Privacy and Security Rules: Understand the HIPAA Privacy Rule (PHI use, individual rights) and Security Rule (administrative, physical, technical safeguards) for effective implementation.
Planning: Define compliance scope, identify risks, assess current controls, and develop a risk management plan.
Design: Prioritize secure data storage, secure transmission, and third-party compliance for reliable architecture.
Engineering: Implement strict data access, encryption, multi-factor authentication, and comprehensive audit trails.
Quality Assurance: Perform security and privacy impact assessments, including penetration testing and regular vulnerability assessments.
Deployment: Use HIPAA-compliant infrastructure (e.g., AWS, GCP), encrypted communication, and secure deployment protocols.
Continuous Monitoring: Post-launch, leverage SIEM systems, regular security reviews, and user education to sustain compliance and enhance data security.
User Trust and Cost Efficiency: Early compliance integration reduces costs, streamlines development, and bolsters user trust in the application’s security practices.
Introduction
Safeguarding sensitive patient information is a critical concern that the Health Insurance Portability and Accountability Act (HIPAA) aims to address. It sets strict standards to ensure the privacy and security of Protected Health Information (PHI). For developers that are building products in the healthcare sector, adhering to HIPAA regulations is not just a legal requirement, but also a fundamental responsibility. Building a HIPAA-compliant product involves much more than adding security features at the end of the development process. Compliance must be integrated into every phase of the product life cycle, from initial planning to the post-launch monitoring. This insight explores how HIPAA compliance can be implemented at each step of the development cycle.
Understanding HIPAA Requirements
To build a HIPAA-compliant product, we need to understand the core regulations governing health information protection. HIPAA has several key rules, but the Privacy and Security Rules are the most critical for product development. The Privacy Rule focuses on how PHI is used and shared. The Security Rule outlines the necessary safeguards that are needed to protect electronic PHI (e-PHI). Understanding both of these is important to building a product that meets the required compliance standards.
1. HIPAA Privacy Rule
The HIPAA Privacy Rule sets national standards to safeguard PHI and regulates its use and disclosure. This rule applies to “covered entities” which include health plans, healthcare providers, and healthcare clearinghouses, as well as their business associates when involving electronic transactions with PHI. The primary objective is to protect privacy while also facilitating the necessary flow of information for high-quality healthcare. It consists of the following key elements:
Covered Entities: The rule includes health plans, healthcare providers, and health clearinghouses. Health plans include those individual and group plans that may cover medical services, such as Health Maintenance Organizations (HMO), Medicare, and Medicaid. Healthcare providers may be any entity that is involved in the transmission of health information electronically. The health clearinghouses process health information between different formats. Additionally, external entities that perform tasks that might involve PHI on behalf of covered entities are also subject to the Privacy Rule’s requirements.
Protected Information: PHI consists of any information that relates to an individual’s health condition, healthcare provision, or payment for healthcare that may be used to identify the individual. However, information that has been disidentified, removing personal identifiers, is not subject to HIPAA restrictions.
Uses and Disclosures of PHI: Covered entities can only use PHI as permitted by the Privacy Rule or with individual authorization. Required disclosures could include letting individuals access their own PHI and disclosures to the U.S. Department of Health and Human Services (HHS) for compliance investigations.
Permitted Disclosures Without Authorization: Individuals must be provided with their own information for treatment, payment, or healthcare operations. This can also be disclosed for public health activities, law enforcement, and facility directories.
Authorization Requirements: Authorization is necessary for certain uses and disclosures such as marketing, and the release of psychotherapy notes.
Minimum Necessary Rule: This rule requires covered entities to limit the use or disclosure of PHI to the minimum necessary to achieve the intended purpose. There are however exceptions for treatment and legal requirements.
Individual Rights: Individuals have the right to request amendments, an accounting of disclosures, restrictions on use, and the right to request confidentiality.
Administrative Requirements: Covered entities are required to designate a privacy officer, develop privacy policies, train their workforce on HIPAA policies, and implement safeguards to protect PHI from unauthorized access.
State Law Preemption: HIPAA supersedes state laws that conflict with its privacy standards unless state laws offer greater protections.
Enforcement and Penalties: The Office for Civil Rights (OCR) enforces the Privacy Rule, with non-compliance leading to fines ranging from $127 to $63,973 per violation, and further criminal penalties for knowing misuse of PHI. This could lead to $250,000 in fines and up to ten years of imprisonment.
2. HIPAA Security Rule
The HIPAA Security Rule established essential standards for protecting e-PHI. This rule applies to entities such as healthcare providers, health plans, healthcare clearinghouses, and business associates who handle e-PHI in electronic transactions. The main purpose of this rule is to ensure the confidentiality, integrity, and availability of e-PHI by implementing technical and non-technical safeguards. It does however offer some flexibility, as it allows entities to tailor their security approaches to their specific needs and associated risks.
The rule outlines three primary types of safeguards: administrative, physical, and technical.
Administrative Safeguards: These involve risk management, access management, security oversight, and workforce training. Entities are advised to conduct risk assessments, appoint security officials, and restrict e-PHI access.
Physical safeguards: These focus on securing the physical facilities and equipment. It would involve restricting access to authorized personnel and establishing proper protocols for the disposal, transfer, and reuse of devices storing e-PHI.
Technical safeguards: These involve access controls, audit trails, integrity checks, and transmission security measures to ensure data integrity during transfers. It also includes preventing unauthorized digital access.
Continuous risk assessment is the cornerstone of the Security Rule, requiring entities to monitor for potential vulnerabilities, assess access logs, update security measures as needed, and document changes. The entities are also responsible for the security practices of their business associates, and hence, contracts often specify these obligations to ensure compliance. In the event of an associate’s breach, the entity is required to take corrective action to mitigate the resulting harm.
Lastly, the entities are also required to maintain documentation of their security policies and risk assessments for at least six years. Generally, HIPAA preempts conflicting state laws unless the state regulations demand stricter protections for health information. These adaptable yet comprehensive safeguards ensure that entities proactively protect their client’s information, which enhances their privacy and security.
The Product Development Life Cycle
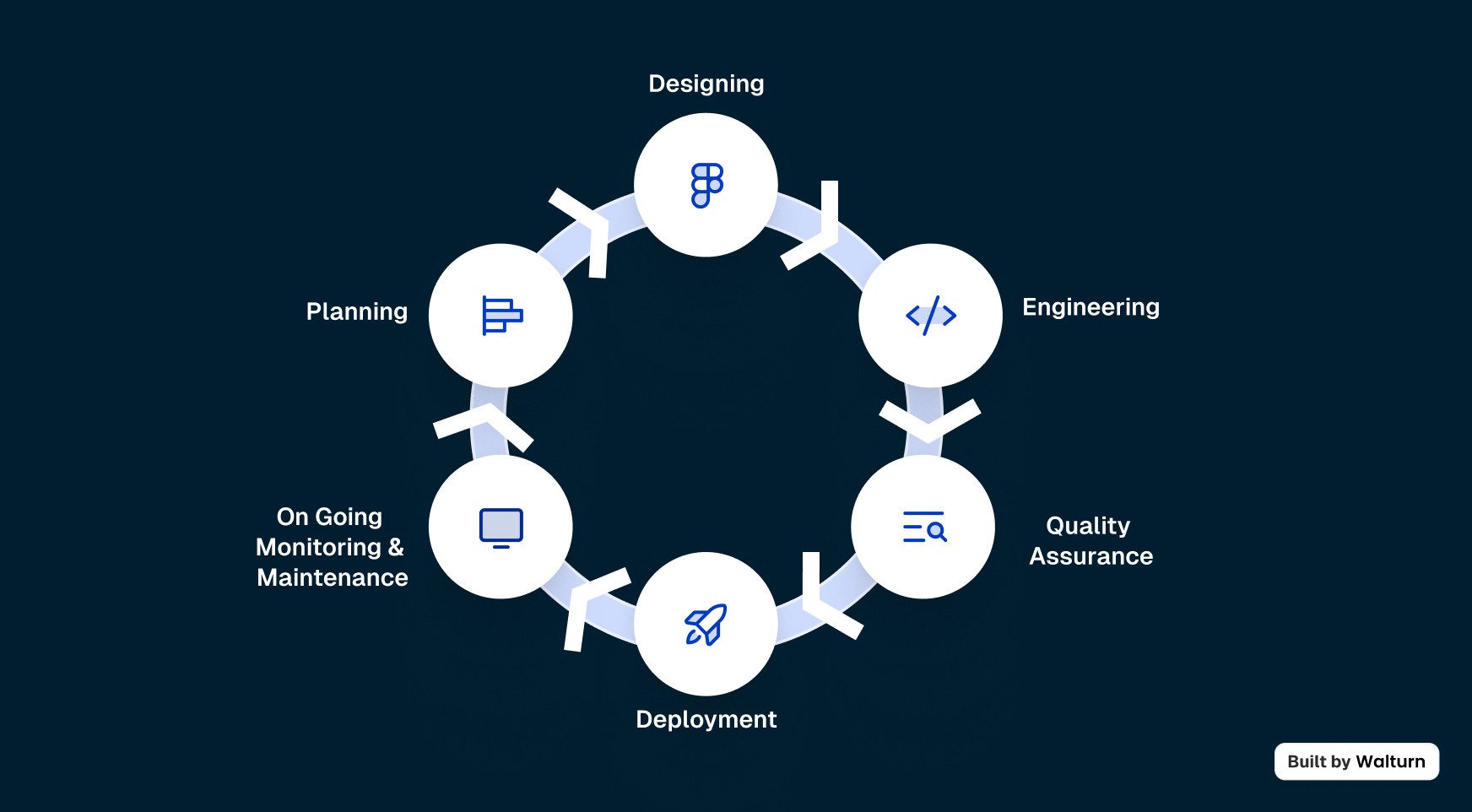
The Product Development Life Cycle is an iterative process that takes an idea and turns it into a product. Here are the six general steps that are involved in the life cycle of a product:
1. Planning
This part sets the roadmap for the rest of the process by clearly defining the product vision, objectives, and target audience. Compliance must also be prepared for at this stage, as it outlines the path the rest of the project will take.
2. Designing
In the design phase, the goal is to figure out how the actual product will look. The designers start by creating the initial sketches of the product and may even go up to establishing a prototype or a blueprint for the product.
3. Engineering
This is where the design comes to life. The development team builds the core functionality of the product and implements all the features that it needs to operate adequately.
4. Quality Assurance (QA)
QA ensures that the product meets the internal and external requirements and standards. All bugs and vulnerabilities are often identified during this stage so that they can be patched before the product is released to the public.
5. Deployment
By this phase, the product has gone through rigorous testing to ensure that it does not contain any obvious bugs or issues. It is released to the public.
6. Ongoing Monitoring and Maintenance
After deployment, the product now enters a phase of constant monitoring and testing. The performance data or user feedback received greatly helps in further fine-tuning the product to fit the changing customer and market needs.
Importance of Early Compliance Integration
Incorporating HIPAA compliance into the product development lifecycle is essential for organizations that handle PHI. By prioritizing compliance from the start, businesses can mitigate risks, streamline processes, and build trust with their users:
Cost Effective: Addressing compliance risks during the initial phases of product development is more cost-effective than attempting to rectify issues after launch. Furthermore, integrating early on reduces the likelihood of redesigns and rework, which saves both time and resources.
Minimized Risks: Identifying compliance requirements at this stage helps organizations see the potential risks associated with handling PHI. This means that they can use the necessary safeguards to mitigate those risks.
Regulatory Adherence: It would also ensure that the product meets regulatory standards, which reduces the chances of costly fines or penalties and helps improve the organization’s reputation.
User Trust: Patients and healthcare providers are increasingly concerned about data security, and being compliant with HIPAA requirements would help build trust and customer loyalty.
Planning
A thorough HIPAA risk assessment early in the development process is important to leverage all the benefits mentioned above. Here are the key steps to follow:
Defining the Scope and Objectives: The scope of the assessment has to be clearly defined, including specific systems, processes, and types of PHI involved. Objectives should then be set that align with the HIPAA requirements.
Identify Potential Threats and Vulnerabilities: The product’s architecture and workflows have to be analyzed so that threats can be identified. Some examples of threats may include unauthorized access, data breaches, or insufficient data encryption.
Assess Current Security Controls: Evaluate the existing measures (if any) in place to protect PHI and see how effective they are in mitigating risks. It must also be ensured that these align with the HIPAA administrative, physical, and technical safeguards mentioned above.
Determine Likelihood and Impact: For the identified risks, the likelihood of occurrence should now be assessed along with the impact it could have on PHI. This will help determine the priority of these risks.
Develop a Risk Management Plan: Create a plan to address the risks identified. It would help to include timelines, assigning responsibilities, and determining necessary resources. This plan will now have to be integrated into the product development timeline.
Regular Review and Update: This whole process should not be considered a one-time effort and regular reviews and updates should be made as the product, threats, and compliance requirements are all subject to change.
Training Development Teams: Technical measures alone cannot ensure HIPAA compliance, and ongoing training of the development team is equally if not more important. Developers need to understand HIPAA requirements related to e-PHI, data encryption, and secure data handling.
Designing
Designing architecture with data privacy and security in mind not only helps with compliance but also helps build trust among the stakeholders. Below are some essential strategies for making secure architecture with the right data management practices.
Data Classification: Begin by categorizing data based on sensitivity. By understanding the nature of the data, you will be able to better judge what level of security it needs.
Secure Data Storage: Choose secure storage solutions that offer built-in security features like access controls and audit logging. Make sure that only authorized users and applications can access sensitive data, and regularly review and update permissions.
Transmission Techniques: Many options can enhance the security of all the data in transit. A Virtual Private Network (VPN) could be used to securely access and encrypt data over untrusted networks. For application-to-application communication, secure protocols like TLS/SSL along with proper authentication mechanisms (such as API keys or OAuth) should be implemented to safeguard data exchanges.
Managing Third-Party Compliance: HIPAA maintains that the business associates or third parties involved with the business that might end up getting access to ePHI should also be HIPAA-compliant. This would mean that the developers would have to look for HIPAA-compliant options when choosing any third-party service provider. Examples could include Web Tracking Technologies and Cloud Databases that the business might leverage.
Engineering
We hope that by now, you are well-versed with HIPAA’s importance and requirements. However, creating HIPAA-compliant applications requires more than simply understanding PHI; developers must also implement policies that tightly control data access, ensure secure user authentication, and establish audit trails. Let us take a look into these key components.
Enforcing Data Access Controls: The Principle of Least Privilege should guide all data access controls. Developers should define access levels strictly according to each role’s necessities. For example, doctors and nurses might be permitted full access to their patients’ PHI, but the administrative or accounting staff may only be given access to specific data required for billing purposes. Access control mechanisms such as Role-Based Access Control (RBAC) may prove useful in segmenting access and minimizing potential breach risks.
Implement Encryption: Utilize encryption techniques to protect data. Encryption algorithms like AES-256 can be used to protect data at rest so that no data remains readable. Using transmission protocols like Transport Layer Security (TLS) can prevent eavesdropping and man-in-the-middle attacks to protect data in transit.
User Authentication and Authorization: HIPAA mandates that authentication methods should be strict enough to protect e-PHI. Developers should implement multi factor authentication (MFA) and enforce strong password policies that require strong passwords. You may consider adding biometric authentication for added security.
Audit Trails and Monitoring: Comprehensive audit trails are essential for HIPAA compliance, as they help trace unauthorized access attempts. Developers have to make sure that each interaction with sensitive data is logged and regularly reviewed.
Quality Assurance (QA)
Compliance testing is a part of the overall software quality assurance that aims not only to align the product with internal standards but also to industry regulations. This type of testing is particularly essential as it helps avoid costly fines in the future, builds user trust, and also shows a commitment to privacy. This is hence a core element that ensures the product meets all the required internal and external standards before it is released.
1. Security Testing
The most obvious part would be security testing. This has two primary parts, penetration testing and regular vulnerability assessments.
Penetration Testing: This generally involves stimulating a real-world attack scenario on the software to identify vulnerabilities that could be exploited by threat actors. This way, developers can find security gaps that might not have been obvious in the previous parts. Since this process essentially mimics cyber attack scenarios, these attempts could also help determine how efficiently the defense team could mitigate risks in a real cyberattack.
Vulnerability Assessments: In addition to penetration tests, regular vulnerability assessments are also crucial. These assessments help in systematically identifying vulnerabilities that could expose sensitive information. The key difference here is that penetration testing aims to exploit vulnerabilities, while vulnerability assessments only identify them. These can then be patched to minimize risks. A sensible approach would be to schedule these assessments regularly.
Security testing plays a fundamental role in compliance as it helps uncover any gaps in security measures, which can then be fixed to help meet regulatory requirements.
2. Privacy Impact Assessments (PIAs)
Another area to focus on is Privacy Impact Assessments (PIAs). These evaluate how personal data is collected, stored, processed, and shared within a software system. They help developers make sure that their data-handling practices are compliant with relevant laws. Conducting PIAs helps organizations address data privacy concerns, minimize risks, and implement safeguards.
If a PIA reveals that certain PHI might be exposed under specific circumstances, the developers could take measures to implement additional encryption, access control, or anonymization. This proactive approach is a must for legal obligations.
Deployment
Deploying or launching healthcare applications requires a secure and structured process to ensure that Protected Health Information (PHI) remains safe during the transition.
1. Deployment Infrastructure
Before the product is deployed, the organization must ensure that the infrastructure meets HIPAA standards. As mentioned earlier, HIPAA requires that the business ensure that its business partners are also HIPAA compliant. This would require the organization to select hosting providers that readily offer Business Associate Agreements (BAA). Some of the options are: Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). To read more about HIPAA compliant databases and services for product engineering, check out this insight.
2. Deployment Environment
The environment has to be “sandboxed” from the development and testing environments to adequately protect sensitive data. All the production comp
The deployment environment must be completely isolated from development and testing environments to protect PHI in production. All production components should be configured to enable encryption for data at rest and in transit, ensuring that sensitive data remains secure across the environment.
3. Deployment Process
The deployment itself should be methodical and secure:
Database Deployment: Set up encrypted database structures first, ensuring data protection from the outset.
Application Code Deployment: Deploy application code through secure, automated pipelines to maintain code integrity. All deployment tools should use encrypted channels, and deployment credentials must be securely controlled and regularly rotated.
Secure Configuration Files: Sensitive information (e.g., database credentials, API keys) should be encrypted and deployed separately from the main application, accessible only to authorized processes.
4. Secure Communication Setup
During deployment, all endpoints must be configured to use secure encryption protocols, such as TLS for web applications. Internal service communication should also occur over encrypted channels, regardless of network proximity, to maintain HIPAA compliance.
5. Final Deployment Steps
The final stage includes enabling the application for live production use. Techniques such as blue-green deployment or rolling updates help transition traffic with minimal disruption, enhancing security and maintaining continuous service. Automated deployments reduce human error, offering a consistent, HIPAA-compliant setup across each deployment.
6. Deployment Verification
Before finalizing, verify that all security measures are active and functional, including encryption, secure communication channels, and isolated network segments. Complete the deployment with thorough documentation of every step, configuration, and security measure, ensuring all actions meet HIPAA compliance requirements.
Ongoing Monitoring and Maintenance
HIPAA compliance does not end once a product launches; it requires ongoing monitoring and proactive maintenance. These are important in detecting and addressing any compliance gaps, security issues, or emerging risks. This way, organizations can identify weaknesses and adapt to the changing requirements.
1. Continuous Monitoring for Sustained Compliance
Continuous monitoring plays a critical role in maintaining HIPAA standards post-launch. This would involve tracking the product’s security, and adherence to regulatory requirements around the clock. Automated monitoring tools like Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and Compliance Monitoring Platforms can be used here. These automatically monitor for unusual activity, unauthorized access attempts, and other issues that help minimize response times and help prevent costly breaches.
With these tools, organizations can receive real-time alerts, generate compliance reports, and quickly address issues. Other than helping with compliance, it also reduces the burden of manual checks, which allows the organization to devote human resources to other important tasks.
2. Post-Launch Audits
Another thing to consider is post-launch audits. They help validate the compliance status of the product. These audits involve systematically reviewing software systems, data handling, and security protocols. The audits are often outsourced to third-party auditors that specialize in compliance standards.
3. Regular Security Reviews
Regular security reviews assess the system’s ability to protect data and maintain integrity. By this point, the importance of regular security checks has been highlighted enough, but here the purpose is to coordinate the security of the product with the latest regulations. For example, if the encryption standards of the product are technically secure and the data is essentially safe, but a change in regulations requires the data to be encrypted differently or with a different algorithm, this has to be taken into account here.
4. User Awareness
Once the product is launched, the users have to be made aware and educated to ensure that security practices are successfully adopted. No amount of security measures can save the users if they fall victim to other attacks such as a phishing attempt. For this reason, the users must be taught about the product’s features and how to use them in a secure manner. Educational efforts—like tutorials, help centers, webinars, and FAQ sections—allow users to take full advantage of the product, which also increases their satisfaction and consumer loyalty. A well-informed user is less likely to encounter issues, which also reduces the need for customer support and hence helps the overall ecosystem of the product.
Conclusion
Ensuring HIPAA compliance in product development is an important process that requires the developers to understand and apply the principles of the Privacy and Security Rules. With the integration of compliance into each step, from design to continuous monitoring, organizations can safeguard protected health information, reduce risks, and build trust. Developers must hence adopt the best practices in building secure architectures and implementing restrictive access controls.
Authors
References
“Blue/Green Deployments - Overview of Deployment Options on AWS.” Docs.aws.amazon.com, docs.aws.amazon.com/whitepapers/latest/overview-deployment-options/bluegreen-deployments.html.
“HIPAA Compliant Cloud Databases and Services for Product Engineering - Walturn Insight.” Walturn.com, 2024, www.walturn.com/insights/hipaa-compliant-cloud-databases-and-services-for-product-engineering.
“How to Conduct a HIPAA Risk Assessment in 6 Steps + Checklist.” Secureframe, secureframe.com/hub/hipaa/risk-assessment.
Office for Civil Rights. “Summary of the HIPAA Security Rule.” U.S. Department of Health and Human Services, 19 Oct. 2022, www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html.
Riaz, Zahid. “HIPAA-Compliant Apps and How to Develop Them?” Bitsol Technologies, 19 Apr. 2023, bitsol.tech/how-to-develop-a-hipaa-compliant-application/.
Saha, Ayesha. “How to Plan for Compliance for Your Product?” InfraCloud, InfraCloud Technologies, 2024, www.infracloud.io/blogs/plan-compliance-for-your-product/.
U.S. Department of Health and Human Services. “Summary of the HIPAA Privacy Rule.” HHS.gov, U.S. Department of Health and Human Services, 2022, www.hhs.gov/hipaa/for-professionals/privacy/laws-regulations/index.html.